
Automated, policy-based, identity and access management blocks system-level attacks and improves operations staff efficiency.
Introduction
Organizations routinely grant broad application and data access to their employees. However, situations such as compromised passwords or employee termination can call for immediate and complete revocation of that access. For large or small organizations, this often means invoking rarely used manual processes, unplanned staff time, and a nagging worry “Did we get everything?” This paper describes Cloud Brigade’s approach to helping a small client organization – from realizing the opportunity to deploying an automated, policy-based system dramatically reducing response time and risk. In addition, they greatly improved the clients onboarding processes for the employees.
The Trigger
After several years expanding the use of shared key security, an internal risk audit revealed manual tracking and update processes were not adequate for the large number of systems under management. For instance, with shared keys, it was necessary to identify all systems at risk due to a compromised key pair and block access. This was a time-consuming task and could also require collaboration with clients IT staff. Once the risk was identified, addressing it became a high priority.
Figure 1 illustrates the complexity of access revocation.
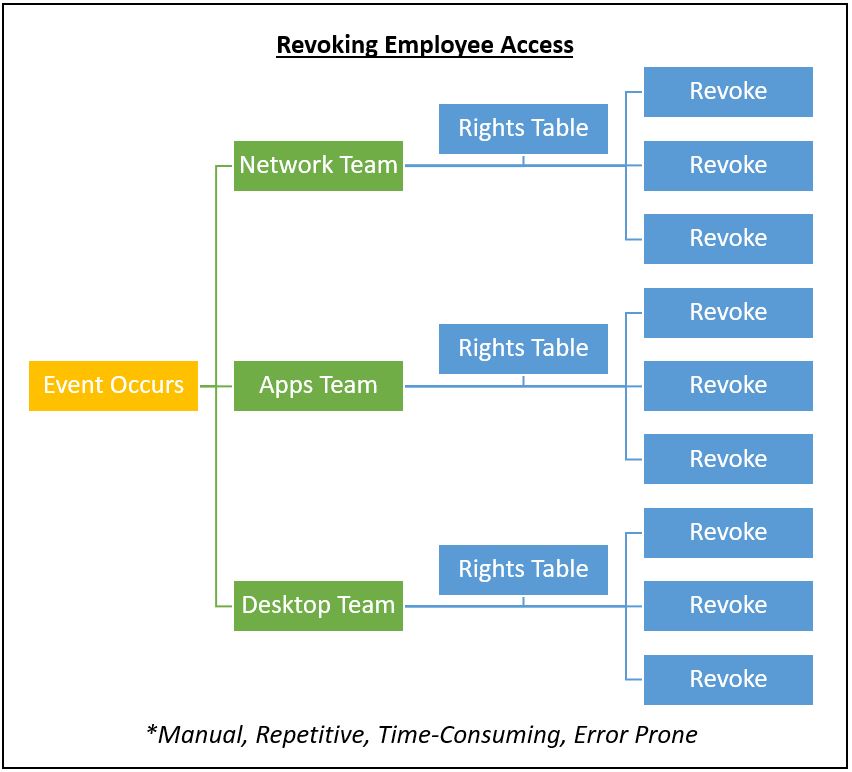
The Risks
Situations like this occur across the business landscape. 60% of companies experience a significant data breach. Such breaches can disrupt businesses at multiple levels:
- Malicious direct damage to applications and data corruption or theft. This can occur very quickly and presents a huge exposure. According to one study, any cyber attack can be fatal.
- Operational time spent addressing the immediate issue, either spent on blocking access or the subsequent cleanup.
- Loss of trust between the IT teams and clients. Impossible to measure, but big and long lasting.
It is one thing to solve a problem, and another entirely to make sure it does not occur again. For business-threatening events such as these, a new approach to access and rights management was needed.
The Troubleshooting Challenge
The first step taken by the Cloud Brigade team was to identify the root cause. Cloud Brigade concluded the biggest risk was posed by slow response time. Factors contributing to slow response time included:
- Shared keys. This system had been implemented to replace password-based access and had been in use successfully for several years. There was a very large number of keys to track.
- Insufficient recordkeeping to identify all in-house systems that any individual employee could access. Part of the issue stemmed from employees shared responsibilities (and keys) coupled with a manual, standalone, siloed access rights tracking system.
- Manual key management. Decommissioning keys needed to be done on a per-system basis, which was time-consuming both due to the number of systems and the inconsistency of processes across in-house and client systems.
- Application updating. All key-based rights were applied manually, system by system. This also applied to remote access and network / WiFi environments. This could not be sustained long term.
Once the issues were understood, Cloud Brigade began to look at options.
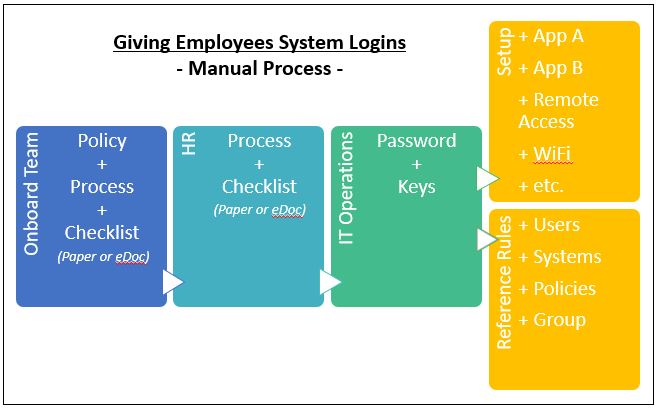
The Onboarding Opportunity
During the initial evaluation, it became clear that the issues tagged to revoking rights mirrored the issues granting them in the first place. Onboarding could also benefit from policy-based rights-granting with the attendant cost savings and error avoidance. As an ongoing task, it could be accurately costed and rolled into project ROI.
Figure 2 illustrates the manual onboarding process.
Evaluating Options
As a quality-driven service provider, thinking ahead on behalf of Cloud Brigade’s customers is part of our tradition. Any solution had to take the risk off the table and deliver additional value to our customers. In this case, it meant automating recordkeeping and access rights revocation to reduce response time and also to streamline onboarding. It also required creating an automated, policy-centric, approach to ensure consistent governance and audit compliance.
From a purely business point of view, the solution needed to be:
- Cloud-based and multi-tenant to support multiple clients
- Easy to configure and manage, since many tasks would repeat consistently
- Seamlessly integrated with the majority of applications already used by clients
- Fast, enabling access rights to be blocked instantly
- Self-service, where customers and staff would minimize load on operations teams
- Priced sensibly so that cost and value could be distributed fairly
After reviewing several options, Cloud Brigade settled on JumpCloud. It provided these capabilities and much more. The next step was to put JumpCloud to work.
Spotlight: JumpCloud
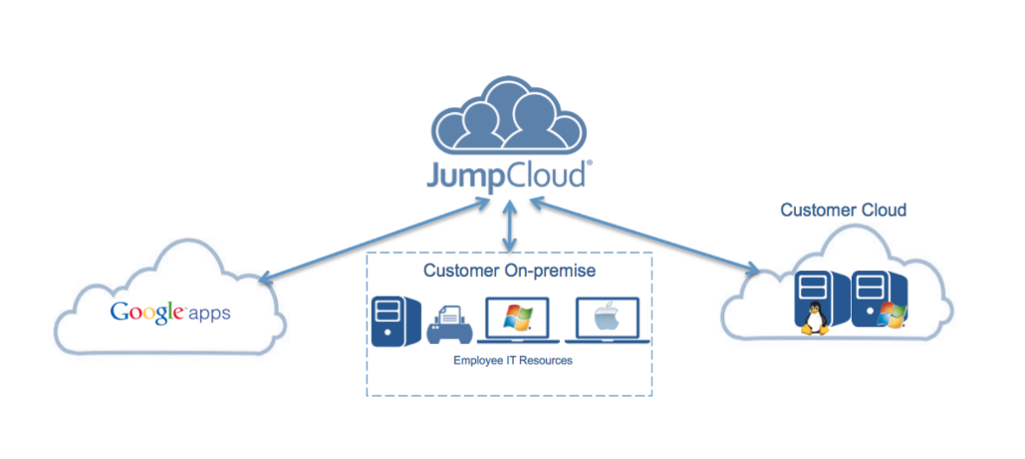
Delivers cloud-based identity and access management, built on a foundation of LDAP directory services. These capabilities were key for Cloud Brigade:
- Unified approach supporting multi-tenant use case
- Centralized identity management with Active Directory integration
- Cross-platform security policy management
- Cloud LDAP to eliminate on-premises risks
- Multi-system automation of access rights management
- Compatible with a wide range of access technologies
- Cloud Radius to simplify remote access
- SSH keys to secure terminal sessions
- Single sign-on to improve user experience
- Multi-factor authentication to reduce password risks
Setting Up
There were several aspects to deployment. Cloud Brigade relied on internal expertise to set up the framework and process to get the job done. This included working closely with the client teams to ensure that policies matched requirements.
Figure 4 shows the general rollout process.
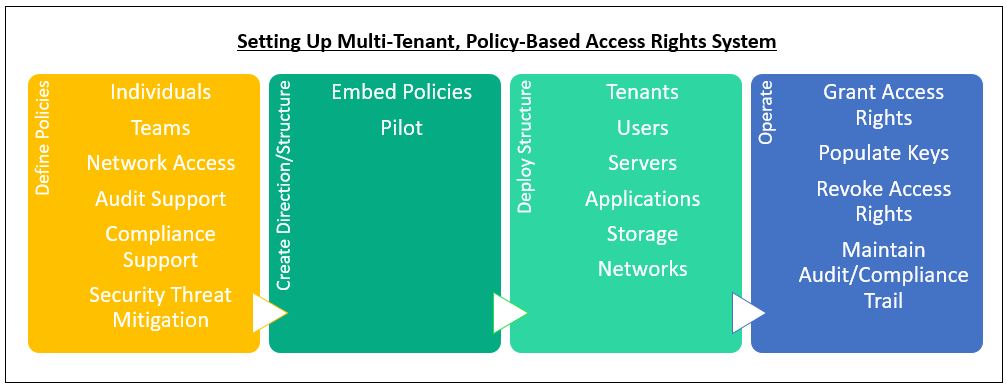
Defining Policies
This is the first step to ensuring sound access rights practices, and includes capturing application inventories and grouping users based on their tasks and access needs. Once these elements were defined, the usage environment could be modeled. Policies were hosted in the JumpCloud LDAP directory. Policy elements include:
- Access details refresh cycles: eliminating stale passwords and shared keys.
- Define reporting needed to support audit compliance.
- Onboarding processes
- Access revocation processes
- Documenting policies to ensure proper usage by clients
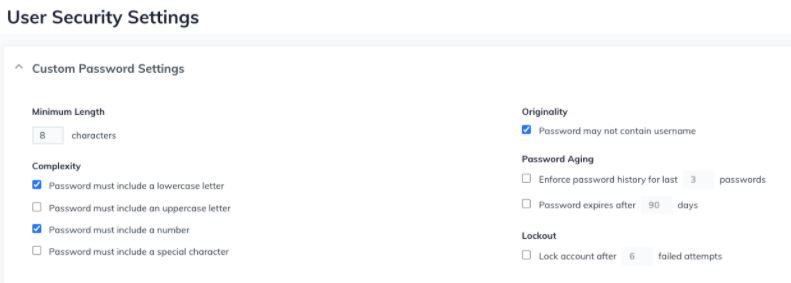
Create Directory Structure
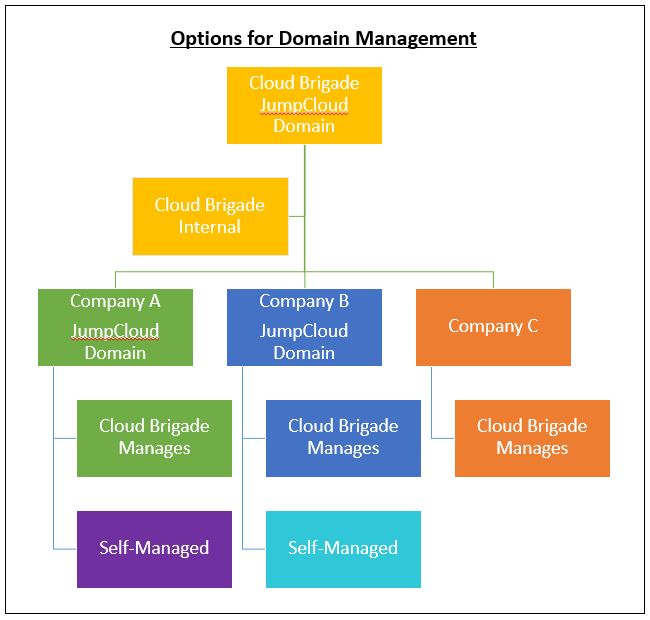
In many cases administration of systems is a shared task between Cloud Brigade and their customers. To meet that requirement, JumpCloud can connect to client systems as well as offering clients the option to set up their own secure JumpCloud domain. This grid of overlapping access rights protects clients by enabling them to make changes for their own environment without the need to get assistance from a service provider like Cloud Brigade.
Figure 5 shows options for combining the client and Cloud Brigade access rights management.
Deploy and Operate
JumpCloud provides connectors to over 450 off-the-shelf applications. Included services enable access services using SAML, oAuth and LDAP protocols. This enabled Cloud Brigade to quickly attach them to JumpCloud. This gave the clients greater levels of protection, as well as ease of use.
- Distribute keys. Based on the policies, systems and roles, keys were distributed across systems and staff to replace the old manual approach. All of this as captured in the directory. Since it is cloud-based, it is immune to on-premises outages.
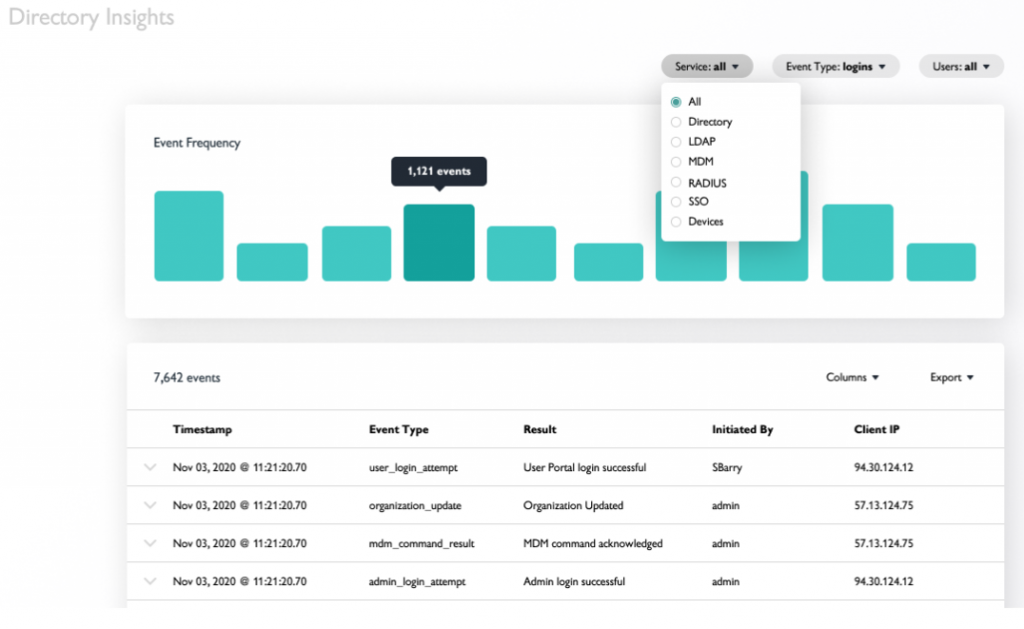
- Operate. Once the initial set up was complete, operations took over. One very useful feature of JumpCloud is self-service key delivery. When staff needs to update keys, they can do it without requiring direct help from the security team. The matching key pair is also distributed to the correct system. Automation yields many operational advantages:
- Continuous recordkeeping, including all self-service key issuance
- Key tracking which can be integrated with other information to provide a complete security audit.
- Simple reporting to clients to ensure service and risk level goals are met.
Results
Cloud Brigade’s client has seen excellent results from their JumpCloud deployment, and it is now a go-to for subsequent new clients. The key take away has been applying a directory based, policy-driven approach to access management. Once only available within corporate IT environments, this approach greatly improves security response time for smaller organizations by relying on rights and roles rather than spreadsheets and access control lists.
It has resulted in:
- Lower operations costs as access becomes self-service
- Better governance and audit to ensure policies are adhered to
- HR- and business-compliant onboarding processes
- Automated security that can lock down access whenever a threat is detected
- Improved customer satisfaction since the system reduces efforts and improves efficiency, while vastly strengthening security
- A stronger partnership with clients to address the evolving threat landscape.
Spotlight: Why Cloud Brigade rather than doing it yourself
While everyone needs robust security for their IT assets and teams, it does take time and effort to understand requirements and convert those to technology, processes and integration. Customers leverage Cloud Brigade’s expertise not just in operations, but their deep understanding of requirements and options. This enables clients to quickly benefit from efficient, secure access management services.
Recap
Moving to policy-based and automated access and identity management is a big project. Organizations can rely on well-defined and mature products and services to lower risks and speed execution.
- Best practices
- Adopt a directory based service to move from manual tasks to policy-driven automation
- Deploy cloud-based service reduces risk and provides greater flexibility
- Tightly defining roles and access rights policy reduces the threat envelope
- Automate policies to enable fast lockdown or change propagation
- Expected results
- Consistent security across all systems
- Lower operational costs
- Sleep better at night
Next Steps
IT security is complex and requires multiple technologies. Cloud Brigade can help you assess issues, set priorities and deploy innovative, bulletproof IT security solutions. Call us for a free fact-finding assessment.